
Europe is an interconnected space, built upon different kinds of infrastructures that organise the circulation of people and “stuff” – capital, commodities, energy, data, etc. Among these infrastructures are large-scale IT systems that allow state authorities to share biographical information (e.g. names, passport numbers) and biometric data on people crossing borders. For example, French border guards may conduct security checks at airports by consulting digitised information that has been previously collected and stored in a database by German police authorities. Migration offices in Spain may access data files created by visa-issuing administrations in Greece. Dutch authorities may access digitised profiles of asylum seekers that have been created when they first arrived in Italy.
”IT systems are not just infrastructures channelling the power to govern international mobility, but also referent objects of government”
Critical studies on security and borders have explored how IT systems (re)configure the management of international mobility and migration. However, we have largely overlooked the maintenance labour through which such digital infrastructures are made functional; labour that supports the flows of data across the spaces where mobile subjects (travellers, migrants, refugees) become targets of control practices. This lack of attention to maintenance leaves some pressing questions unanswered. Do IT systems always perform as expected by those actors who have previously designed them or do they counter-perform and, potentially, fail after their deployment? If infrastructures, such as IT systems, their components, interdependencies and liveliness become visible when they malfunction and break down, then what does it take to make them invisible – docile machines that operate according to the rules and procedures specified in the documents that lay down their design characteristics?
In my article “Governing Border Security Infrastructures: Maintaining Large-Scale Information Systems” (Security Dialogue), I seek to answer these questions by presenting in-depth empirical material from my research on eu-LISA. This is the EU Agency entrusted with the operational management (i.e. maintenance and protection) of IT systems deployed for border and migration management purposes. By synthesizing elements of Michel Foucault’s work on biopolitics and governmentality with ideas inspired by the New Materialisms movement, I argue that IT systems are not just infrastructures channelling the power to govern international mobility, but also referent objects of government – both “rulers” that monitor and govern bodies on the move, and unruly infrastructures that are themselves governed through maintenance.
The observation that IT systems require maintenance to function should not come as a surprise to scholars investigating the digitisation of border security and migration management. Perhaps it is the mundanity of maintenance that makes it invisible and unquestioned. Yet, overlooking this process hinders a more a complete appreciation of ongoing “technological work”[1] through which digitised borders are implemented and made functional. This technological work matters politically because it conditions the control and surveillance of subjects on the move, and thus sustains the power to govern international mobility by digital means. My goal is, then, to broaden the research agenda exploring “border security as practice”[2], by directing attention towards a neglected group of actors who, by maintaining IT systems, seek to sustain the continuity of data-based controls that performatively produce the borders regulating international mobility.
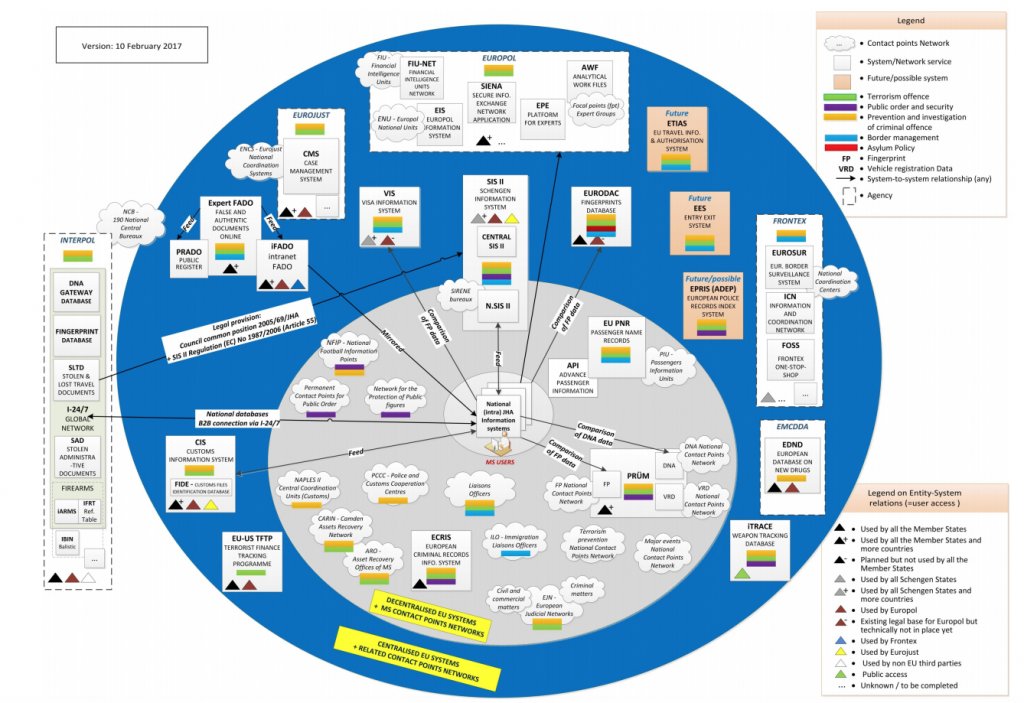
Overview of the information exchange environment in the field of EU Justice and Home Affairs (JHA)
Visit link to see larger image
Source: Council of the European Union (2017) Document Number 6253/17
[1] Walters W (2011). Rezoning the global: technological zones, technological work and the (un-)making of biometric borders.” In Squire V (ed) The contested politics of mobility. Borderzones and Irregularity. London: Routledge: 51–73.
[2] Côté-Boucher K, Infantino F, and Salter MB (2014) Border security as practice: an agenda for research. Security Dialogue 45(3): 195–208.